1、生成泛域名证书脚本
#!/bin/bash
# 配置变量
DOMAIN="mydevweb.local"
DAYS=730
CA_DAYS=3650
echo "=== 生成根证书 ==="
openssl genrsa -out ca.key 2048
openssl req -x509 -new -nodes -key ca.key -sha256 -days $CA_DAYS \
-out ca.crt -subj "/C=CN/ST=State/L=City/O=Organization/CN=${DOMAIN} CA"
echo -e "\n=== 生成泛域名证书 ==="
openssl genrsa -out ${DOMAIN}.key 2048
# 创建CSR配置文件
cat > csr.conf << EOF
[ req ]
default_bits = 2048
prompt = no
default_md = sha256
distinguished_name = dn
[ dn ]
C = CN
ST = State
L = City
O = Organization
CN = *.${DOMAIN}
[ req_ext ]
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = *.${DOMAIN}
DNS.2 = ${DOMAIN}
EOF
# 创建扩展配置文件
cat > cert.conf << EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = *.${DOMAIN}
DNS.2 = ${DOMAIN}
EOF
# 生成证书
openssl req -new -key ${DOMAIN}.key -out ${DOMAIN}.csr -config csr.conf
openssl x509 -req -in ${DOMAIN}.csr -CA ca.crt -CAkey ca.key -CAcreateserial \
-out ${DOMAIN}.crt -days $DAYS -sha256 -extfile cert.conf
echo -e "\n=== 生成完成 ==="
echo "证书文件:"
echo " - ca.crt (根证书,需要导入到系统/浏览器信任)"
echo " - ${DOMAIN}.crt (服务器证书)"
echo " - ${DOMAIN}.key (私钥)"
echo " - ${DOMAIN}.csr (证书签名请求)"
# 可选:生成PEM格式(包含证书链)
cat ${DOMAIN}.crt ca.crt > ${DOMAIN}.pem
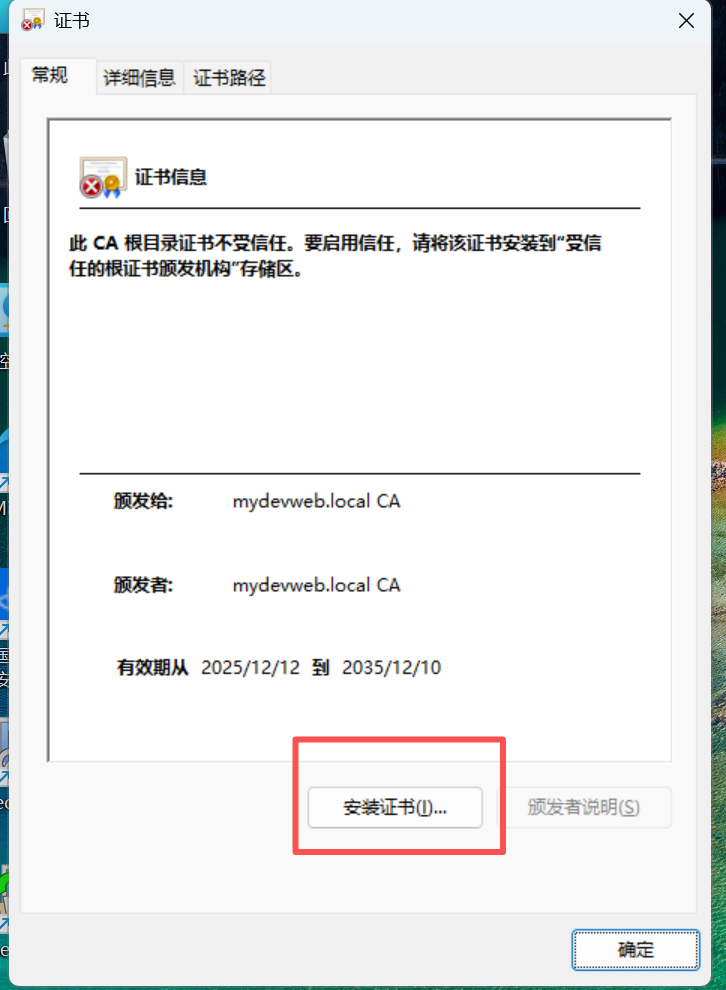
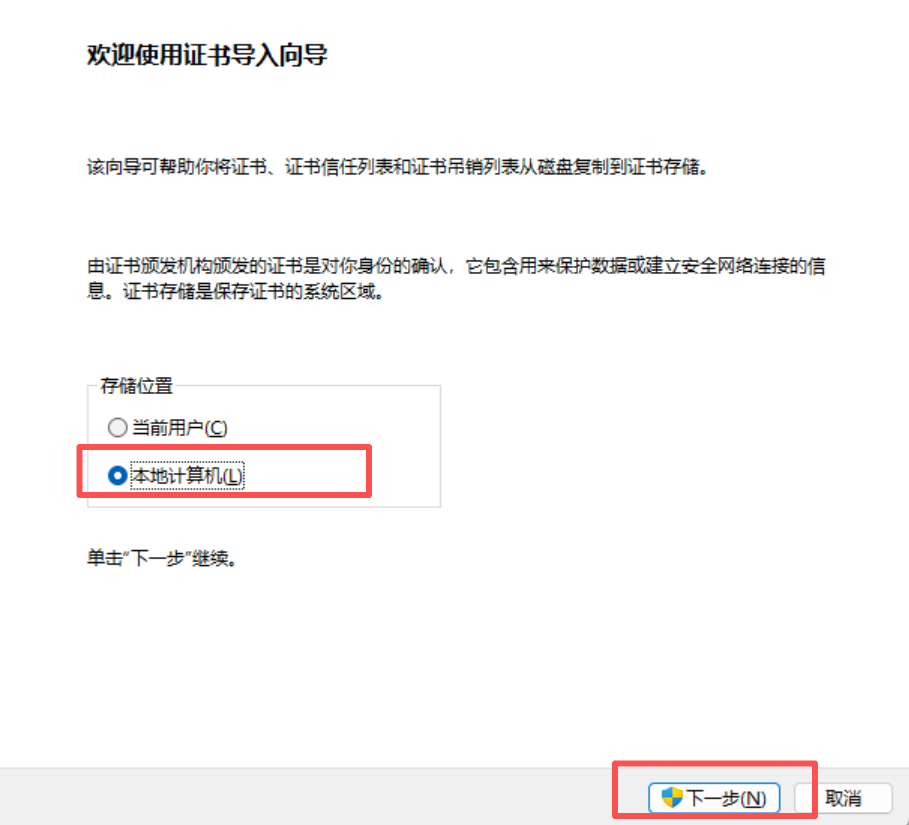
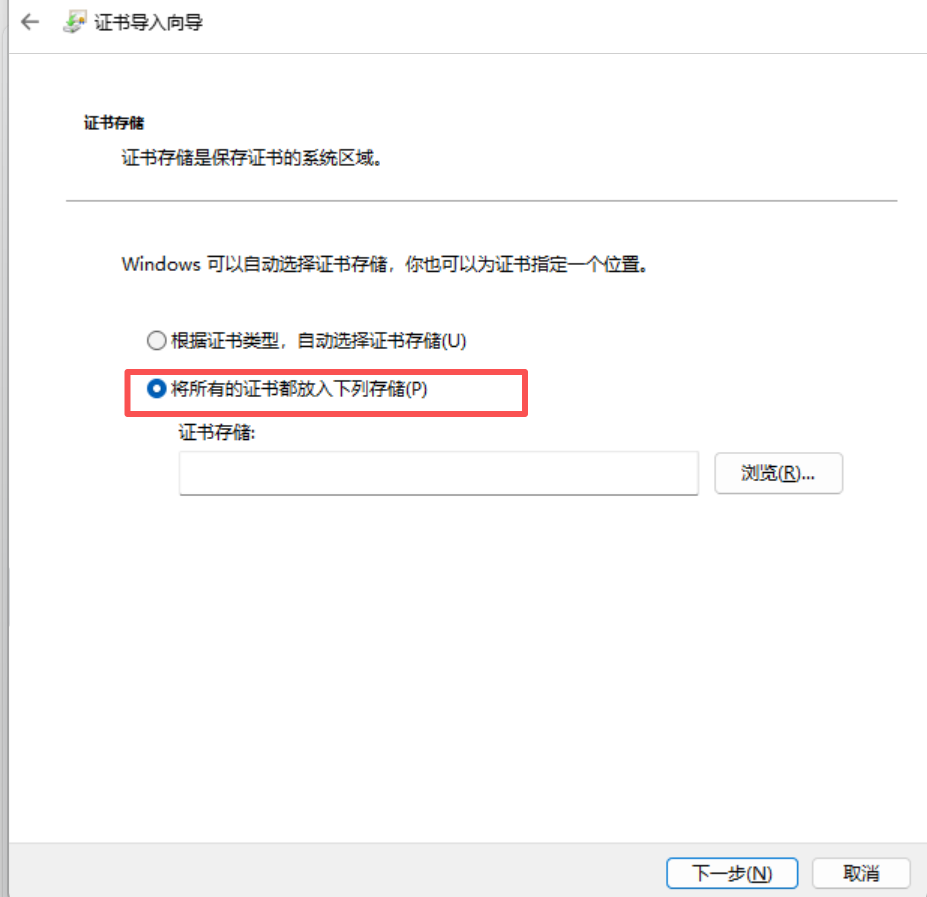
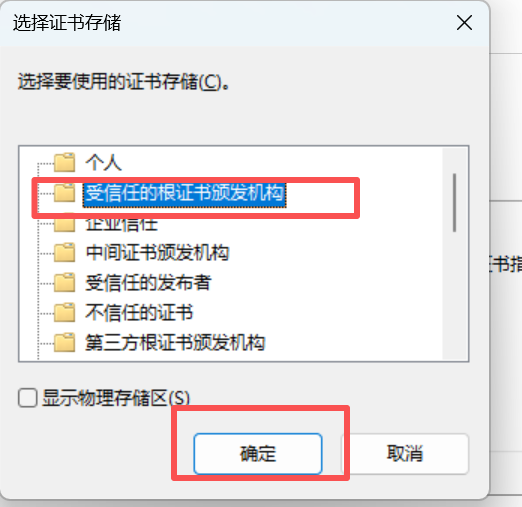
2、操作系统配置信任证书
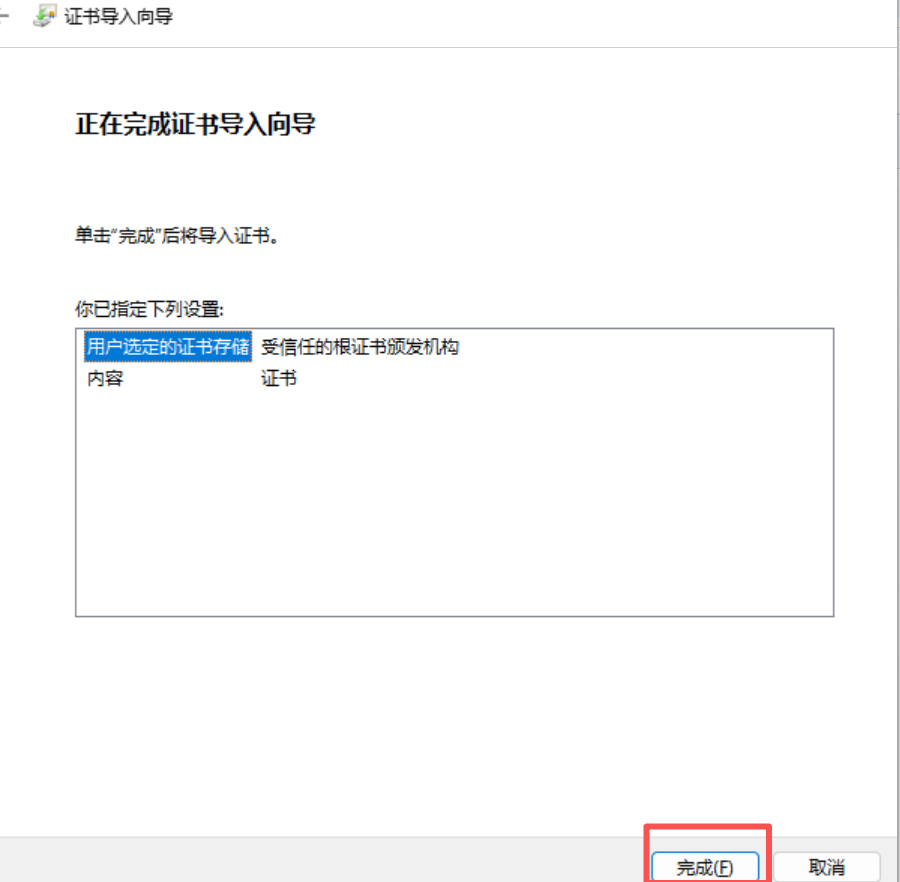
windows信任根证书ca.crt

redhat系linux
sudo cp ca.crt /etc/pki/ca-trust/source/anchors/
sudo update-ca-trust
debian系linux
sudo cp ca.crt /usr/local/share/ca-certificates/
sudo update-ca-certificates




评论区